
Without much hesitation, it could be said that ExpressVPN and NordVPN are the champions of today’s VPN industry. Both of these VPN solutions have been around for a while, they offer great value for their price and plenty of highly advanced options. However, this is also what makes it hard to choose between the two. So, which one is better – ExpressVPN or NordVPN? Well, we are going to help you with this by comparing these two VPN services. Welcome to our ExpressVPN vs NordVPN comparison!
First, here’s a breakdown of the most important aspects of ExpressVPN and NordVPN. Take a look at the following table to compare their most prominent features.
| ExpressVPN | NordVPN | |
| Jurisdiction | The British Virgin Islands | Panama |
|---|---|---|
| Logs | No logs collected, whatsoever. | No logs collected, whatsoever. |
| Number of Servers | 3,000+ servers in 90+ countries. | 5,200+ servers in 60+ countries. |
| Parallel Connections | 5 | 6 |
| Encryption Standards | AES-256; OpenVPN, PPTP, L2TP/IPSec | AES-256; OpenVPN, IKEv2/IPsec |
| Speed Reduction | 19% on average. | 38% on average. |
| P2P Support | YES | YES |
| Supported Platforms | Windows, macOS, Linux, Android, iOS, Web browsers, and routers. | Windows, macOS, Linux, Android, iOS, Web browsers, and routers. |
| Visit | ExpressVPN | NordVPN |
Next, take a look at the final scores from our reviews of these two VPN providers. Then, keep on reading to dive deep into the specifics.
| ExpressVPN | NordVPN | |
| Jurisdiction, Reputation | 10/10 | 10/10 |
|---|---|---|
| Supported Platforms | 10/10 | 10/10 |
| Installation Process | 10/10 | 10/10 |
| Prominent Features | 9.5/10 | 10/10 |
| Server Count | 8.5/10 | 10/10 |
| Ease of Use | 10/10 | 9/10 |
| Media Streaming & Torrenting Support | 10/10 | 7/10 |
| Security & Privacy | 10/10 | 10/10 |
| Speed & Performance | 9/10 | 7.5/10 |
| Customer Support | 10/10 | 10/10 |
| Pricing | 9/10 | 8/10 |
| Overall Score | 9.6/10 | 9.2/10 |
We had no choice but to create the ultimate head-to-head to find out which VPN deserves to sit on the throne. So, keep on reading our ExpressVPN Vs NordVPN comparison.
ExpressVPN vs NordVPN (2019) – Which One’s Better?
Just like in our reviews of these two VPN giants, we’ll be taking a look at every important aspect of using a VPN service. So, let’s jump right in.
Background, Jurisdiction & Reputation

When choosing between different VPN services, you’ll want to check their background information first. Always go for the VPN outside of the 14-Eyes Alliance, and pick the one with no data leaks in the past.
- ExpressVPN: This VPN brand comes from the British Virgin Islands. It’s outside of the 14-Eyes Alliance, and it’s known for its dedication to its users. ExpressVPN has had its services reviewed by an independent party in the past, and it’s one of a few certified no-logs VPN services. And finally, this VPN has been providing free access to users from ‘problematic’ areas of the world during certain times, allowing them to unblock websites and get information from the outside world.
- NordVPN: This VPN comes from Panama, and it’s generally known for its transparency. This is yet another independently audited VPN service, so you can be sure that no data logging is happening in the background. In addition, NordVPN is always quick to resolve any problematic points in its apps via prompt updates. And let’s not forget the fact that this VPN is the recipient of numerous VPN-related awards.
Winner: Both ExpressVPN and NordVPN are highly reputable brands – so we’ll call it a tie. No manner which one you pick, you can be sure that you’re private and sensitive data is being handled in the best way possible.
Supported Platforms & Devices

Depending on how many devices you want to connect to the Web, you need to be careful when picking a provider. Lucky for you, both ExpressVPN and NordVPN deliver what their promise.
- ExpressVPN: This VPN provider is based on the OpenVPN protocol, which ensures broad system compatibility. You can count on a wide range of native apps that can be installed on all popular desktop and mobile operating systems. There are also apps for Linux and even Blackberry. Of course, OpenVPN ensures that ExpressVPN can be installed even on VPN-compatible routers. Also, you can use this VPN service on up to 5 devices at the same time.
- NordVPN: When it comes to supported devices, NordVPN does not disappoint. It offers highly polished apps for every popular platform out there. And since OpenVPN is present here as well, you can even install in on your router. NordVPN can be used on 6 devices at the same time, which gives it a small advantage over its direct competitor.
Winner: It’s hard to pick a winner in this category since both of these VPNs are present on pretty much any platform. If we really want to nitpick, we’d go with ExpressVPN since it brings hugely helpful installation guides on its official website.
Installation & Initial Configuration

Next, let’s take a look at how easy it is to install and configure these VPN clients. After all, you want to begin using a secure connection without any hassle.
- ExpressVPN: After signing up for a new ExpressVPN account, you can proceed to download the app. It doesn’t contain any bloatware and takes very little hard drive space. You can install and begin using the application in less than a few minutes of your time. The same applies to desktop and mobile devices. It’s also worth noting that ExpressVPN comes with numerous helpful guides that show how to install this VPN on a wide range of devices, including routers.
- NordVPN: Just like its biggest competitor, NordVPN brings a highly polished installation method. The installation file is quite small so you don’t have to have a fast Web connection. Aside from desktop and mobile devices, NordVPN can be installed on compatible routers. However, we feel that this VPN provider should have invested more time in coming up with instructions and tutorials. Some of those are quite basic, making you turn to their support team for answers.
Winner: Once again, picking a clear winner is quite hard. However, we have to say that both ExpressVPN and NordVPN bring equally simple installation. Even complete newbies won’t have a hard time installing and getting started with these VPNs.
Prominent Features

Our next category of the ExpressVPN Vs NordVPN comparison contains the most prominent features. So, let’s jump right in.
- ExpressVPN: The best thing we can say about ExpressVPN is that it just works. It is rock-solid, reliable, and nails the fundamentals. Aside from that, you’ll get to use a highly polished kill-switch as well as all currently available VPN protocols. And when it comes to the most advanced features, ExpressVPN brings split-tunneling. Where this VPN truly shines is the way it lets you handle these features. It’s not overly simple but even inexperienced users will be able to dive into advanced security-related technologies.
- NordVPN: NordVPN, on the other hand, is almost overflowing with features. We’ve talked about the kill-switch, double VPN, and Onion servers, but that’s just the start. There are special obfuscation servers, anti-DDoS servers, a paid option for dedicated IP servers, and more. All in all, you’ll find plenty of features here that can satisfy even the most demanding users.
Winner: Even though both ExpressVPN and NordVPN are hugely capable VPN services, we have to say that NordVPN is the winner of this round. You get a constant stream of new features and even ad-blocking is included.
Server Count

Knowing the number of servers you’ll have at your disposal is a good thing. However, you also need to know in what way these servers are distributed. To check other options, take a look at our article on VPNs with the highest number of servers.
- ExpressVPN: This provider manages a network of over 3,000 servers spread across 90+ countries. This is more than enough to meet your every need. Also, you get to test the speed of each server and pick the one with the best result. This translates to a pleasurable media streaming experience and can be especially helpful if you want to download large files.
- NordVPN: Without any doubt, NordVPN is the most powerful VPN in terms of servers. It has more than 5,200 servers spread across the globe. Interestingly enough, this doesn’t translate to a throttle-free experience. Since double-encryption is involved, you’ll be using two secure servers at any moment. Therefore, some throttling is still present.
Winner: Even though it doesn’t have as many as NordVPN has, ExpressVPN should meet your every need. Having 3,000+ servers is an incredible power to have under your fingertips. In addition, ExpresVPN’s servers are present in 90+ countries, which is one of its biggest selling points.
Ease of Use

Both VPNs have exceptional user interfaces, and they cater to almost every type of device under the sun. They’ve both invested a lot of time into refining their designs and making sure the experience is consistent across all clients and even their websites.
- ExpressVPN: This provider has a simple and elegant design, with no clutter to speak of. The main screen has a big, bold power button that will connect to a ‘Smart Location.’ With a single click or tap, you can connect to the Web anonymously, without needing to mess around with settings. If you do choose to pick your own server location, there is a shortlist of recommended servers to try, or the full list of ExpressVPN’s global army of servers. There’s no immediate way to know what server to choose, but you can run a speed test (it will take about five minutes) on all the servers to determine the fastest options. And finally, ExpressVPN is limited to just three simultaneous connections, although their router client will protect every device connected to it.
- NordVPN: This VPN greets you with a stylishly designed map of the world and a connection wizard that will find the best server for your specific need (like P2P or security). We absolutely adore how NordVPN organizes its servers into types and countries. It is always happy to make life simple by connecting you to the best server, but it also gives you the freedom to click on a country or type and get an overview of those available servers. You’ll find distance and server load to help you make the perfect manual choice. NordVPN allows double the amount of simultaneous connections (six), so you should be able to install it on pretty much every device that you own. And have a slot or two available for your friends.
Winner: Both VPNs offer exceptional ease of use, but ExpressVPN digs beneath the surface level to provide a richer experience. They are both exceptional, but ExpressVPN edges it.
Media Streaming & Torrenting Support

Planning to stream media on the Web? Do you still want to use Netflix and other media streaming services, even while using a VPN? If that’s so, keep on reading.
- ExpressVPN: We strongly believe there’s no better VPN for streaming than ExpressVPN. It can unblock pretty much any website out there, including Netflix, Hulu, Amazon Prime Video, BBC iPlayer, and plenty more. Also, this VPN fully supports torrenting via all of its servers.
- NordVPN: Even though it’s being advertised as a streaming-friendly option, that’s not exactly the case in practice. Even though you can unblock a nice list of websites, it can be tedious to find the one that works with the website you want to unblock. In addition, NordVPN supports torrenting only via specialized servers.
Winner: It’s clear that ExpressVPN wins this round. Without any doubt, this is the most capable VPN service for media streaming and downloading torrents.
Security & Privacy

Privacy and security are the main reasons why people turn to VPNs. Thankfully, you can rest easy knowing that by using ExpressVPN or NordVPN, you are in safe hands.
- ExpressVPN: Aside from the standard VPN features, ExpressVPN has a very powerful Kill-Switch that prevents data leaks when your VPN connection drops. Then, you can utilize different VPN protocols (OpenVPN, PPTP, L2TP/IPSec), depending on if you want to prioritize speed or security. There are no data leaks as per our tests, and this VPN comes with a privacy policy that nicely explains everything that happens in the background.
- NordVPN: The flagship feature of NordVPN is double encryption, which is something that’s rarely seen these days. This means that you shouldn’t have any concerns when it comes to privacy. There are also two VPN protocols to choose from, so not as many as ExpressVPN offers. Still, NordVPN offers more than what any average user would ever need, and its list of features would make even the most highly demanding users happy.
Winner: Once again, ExpressVPN is one step ahead of its biggest competitor since it offers a larger number of VPN protocols. Even though both of these will keep you safe and sound online, ExpressVPN wins this round.
Speed & Performance

Security and privacy are great but not when they come at the cost of speed. If you’re going to connect to servers on the other side of the world, you’re going to experience slower speeds, but a great VPN will minimize the slowdown. To check out other options, here’s our overview of the fastest VPN providers.
- ExpressVPN: There are two ways to connect to a remote server via ExpressVPN. You can run a speed test and then connect to a server manually. Or, you can let the application decide which server works the best in any given moment. As a result, you’ll experience throttle-free Web browsing and media streaming. In case you have a fast connection, to begin with, 4K streaming is not an unreachable dream. As per our tests, this VPN slowed us down by 19% on average, which is a highly respectable result.
- NordVPN: This VPN prioritizes the security of your data of performance (speed). By default, you’ll get to use double-encryption that will keep your data 110% safe. However, this setup might be on overkill for average home users. And as a result, some throttling will happen. As our NordVPN review will you, this VPN slowed us down by 38% on average, so it’s clear who’s the winner of this round.
Winner: Without any doubt, ExpressVPN wins this round. This is one of the fastest-performing VPN services, offering great performance no matter which VPN protocol you decide to use.
Customer Service

We were very impressed by the levels of support that these VPNs offer to subscribers. No matter which one to pick, you’ll receive answers to your question. The only difference here is how long you’ll need to wait to get an answer.
- ExpressVPN: ExpressVPN was lightning fast in responding via live chat (which is 24/7) and via form submission on their website. You may not even need to talk to anyone because their website contains plenty of tutorials and guides to help you set up, resolve, and explain just about everything related to the service.
- NordVPN: As good as ExpressVPN’s live chat was, we were even more impressed with NordVPN. Their support members were just as fast and we didn’t feel like they were reading from a script. However, responses to our form submissions took much longer (six hours versus ExpressVPN’s one hour) during our testing period.
Winner: When you get stuck and need a hand, ExpressVPN is doing the most to help you get back on track. However, it’s worth noting that both of these provide top-level customer service, and your questions will be answered in a timely manner.
Pricing

ExpressVPN and NordVPN are maybe two of the more expensive VPN offerings, but having spent a lot of time with both, we feel that they are worth every penny.
- ExpressVPN: At the moment, the most affordable plan of this VPN provider will cost you $99.95 per year (which comes down to $6.67 per month). For that money, you will receive full protection without any caveats. This means having access to 24/7 customer support and using the application without any bandwidth limitations. ExpressVPN comes with a 30-day money-back guarantee and you can use it on up to five devices at the same time.
- NordVPN: To make a direct comparison, you should know that NordVPN has a yearly plan, priced at $83.88 (so, it’s $6.99 per month). However, you’ll find other long-term plans which bring the price down to $2.99 per month if you get a 3-year plan. Even though this pricing structure helps you save in the long-term, it requires a significant upfront investment.
Winner: These two VPN services bring comparable prices. When it comes to their annual plans, ExpressVPN is the more affordable option. However, NordVPN brings the price of its service down via its 2- and 3-year plans.
ExpressVPN vs NordVPN: Which One Should You Pick?
ExpressVPN and NordVPN are, in our opinion, the best of the best. You can’t go wrong with whichever choice you make, but there can be only one winner, and that is ExpressVPN.
ExpressVPN has the looks of a champion and delivers the anonymity and security that you’d want from a quality VPN service. It’s just as easy to use as NordVPN (newbie-friendly) but also offers deeper functionality for those who want a bit more control over their VPN. Even though NordVPN is more affordable, it doesn’t really offer the same level of service or functionality as ExpressVPN does. So, go ahead and sign-up for ExpressVPN today. You won’t regret it!
 Each of those new interfaces expands the cyber attack surface of your home network. The more interfaces you have, the more vectors you have for the bad “hackers” to get in. So consider the risks of new devices before you buy them.
I personally have very little in the way of IoT tech in my home. I have a smartphone which, of course, doubles as a device that can be used to spy on me. The cybersecurity risks of my phone are similar to the risks my PC has, but it’s a desktop and it can’t be used to track my movements when I’m not home.
I have a “dumb” TV, but it operates as a display for my PS4, PS3, and Raspberry Pi-based Retro Pie console. Those consoles are all internet-connected, and my PS4 also has a PlayStation Camera that could be intercepted to watch me while I’m in my bedroom.
Aside from my router, those are all the internet-connected devices that I have. As a cybersecurity professional, you might assume that I want to have all the latest toys. But, in fact, being a cybersecurity professional means that I’m cautious about new toys.
You could choose to cover your home in Google Home speakers and deploy internet-connected security cameras or whatever you want. Just keep in mind that those could be new means for cyber attackers to interfere with your life—and for security to harden accordingly.
Each of those new interfaces expands the cyber attack surface of your home network. The more interfaces you have, the more vectors you have for the bad “hackers” to get in. So consider the risks of new devices before you buy them.
I personally have very little in the way of IoT tech in my home. I have a smartphone which, of course, doubles as a device that can be used to spy on me. The cybersecurity risks of my phone are similar to the risks my PC has, but it’s a desktop and it can’t be used to track my movements when I’m not home.
I have a “dumb” TV, but it operates as a display for my PS4, PS3, and Raspberry Pi-based Retro Pie console. Those consoles are all internet-connected, and my PS4 also has a PlayStation Camera that could be intercepted to watch me while I’m in my bedroom.
Aside from my router, those are all the internet-connected devices that I have. As a cybersecurity professional, you might assume that I want to have all the latest toys. But, in fact, being a cybersecurity professional means that I’m cautious about new toys.
You could choose to cover your home in Google Home speakers and deploy internet-connected security cameras or whatever you want. Just keep in mind that those could be new means for cyber attackers to interfere with your life—and for security to harden accordingly.
 It’s unlikely that a cyber attacker will intercept your internet connection physically. Chances are if they want access to your internet connection, they’ll look for your WiFi.
Go to your router. If you have WiFi, your router assigns an SSID (a way of naming WiFi signals) and password to your account. Your router came with a default SSID and password. If you’re using that default SSID and password, you have a seriously dangerous security vulnerability in your home network and must fix it right away.
It’s unlikely that a cyber attacker will intercept your internet connection physically. Chances are if they want access to your internet connection, they’ll look for your WiFi.
Go to your router. If you have WiFi, your router assigns an SSID (a way of naming WiFi signals) and password to your account. Your router came with a default SSID and password. If you’re using that default SSID and password, you have a seriously dangerous security vulnerability in your home network and must fix it right away.
 The default SSIDs and passwords associated with the device model of your router and your internet service provider are easy to find on the internet.
The default SSIDs and passwords associated with the device model of your router and your internet service provider are easy to find on the internet.  Source:
Source:  If you don’t have a VPN set up yet, or if you’re considering changing your VPN provider,
If you don’t have a VPN set up yet, or if you’re considering changing your VPN provider, 
 I work for an antivirus company, so I won’t recommend anything specific. Instead, I’ll direct you to
I work for an antivirus company, so I won’t recommend anything specific. Instead, I’ll direct you to  Laptops often have built-in webcams, and you may also have cameras for your Google Home or Amazon Echo, or as a separate peripheral connected to your desktop PC. Disconnect all cameras or cover them with duct tape when you’re not using them. It’s also a good idea to disconnect your Google Home or Amazon Echo speakers when you’re not at home.
By disconnecting or covering cameras and speakers in your home network when you’re not using them, you’re making it more difficult for cyber attackers to watch or listen to you in a space that should be private. There are lots of malware and man-in-the-middle cyber attacks that can grant the bad guys a way to violate your privacy.
My advice is to limit your “cyber attack surface” as much as possible by reducing it in ways that are feasible.
Credit card and personal banking credentials are also highly attractive to cyber attackers. Sometimes people store this sort of data in their smart TVs and video game consoles. My advice is to use your credit card as infrequently as possible.
If you have services that you pay for, such as Netflix, Hulu, Amazon Prime, PlayStation Network, Xbox Live, or Spotify, you can often pay for them using gift cards.
Laptops often have built-in webcams, and you may also have cameras for your Google Home or Amazon Echo, or as a separate peripheral connected to your desktop PC. Disconnect all cameras or cover them with duct tape when you’re not using them. It’s also a good idea to disconnect your Google Home or Amazon Echo speakers when you’re not at home.
By disconnecting or covering cameras and speakers in your home network when you’re not using them, you’re making it more difficult for cyber attackers to watch or listen to you in a space that should be private. There are lots of malware and man-in-the-middle cyber attacks that can grant the bad guys a way to violate your privacy.
My advice is to limit your “cyber attack surface” as much as possible by reducing it in ways that are feasible.
Credit card and personal banking credentials are also highly attractive to cyber attackers. Sometimes people store this sort of data in their smart TVs and video game consoles. My advice is to use your credit card as infrequently as possible.
If you have services that you pay for, such as Netflix, Hulu, Amazon Prime, PlayStation Network, Xbox Live, or Spotify, you can often pay for them using gift cards.
 Alternatively, there are credit card gift cards you can use to pay for most online services. Use gift cards as much as possible. The worst-case scenario with a gift card is that a cyber attacker steals its value from you, whether it’s $100 or whatever.
The worst-case scenario with a conventional credit card is much more expensive than $100. If a cyber attacker acquires that data, they could access your personal banking and wipe your bank accounts dry or engage in identity fraud where they pretend to be you online.
Alternatively, there are credit card gift cards you can use to pay for most online services. Use gift cards as much as possible. The worst-case scenario with a gift card is that a cyber attacker steals its value from you, whether it’s $100 or whatever.
The worst-case scenario with a conventional credit card is much more expensive than $100. If a cyber attacker acquires that data, they could access your personal banking and wipe your bank accounts dry or engage in identity fraud where they pretend to be you online.
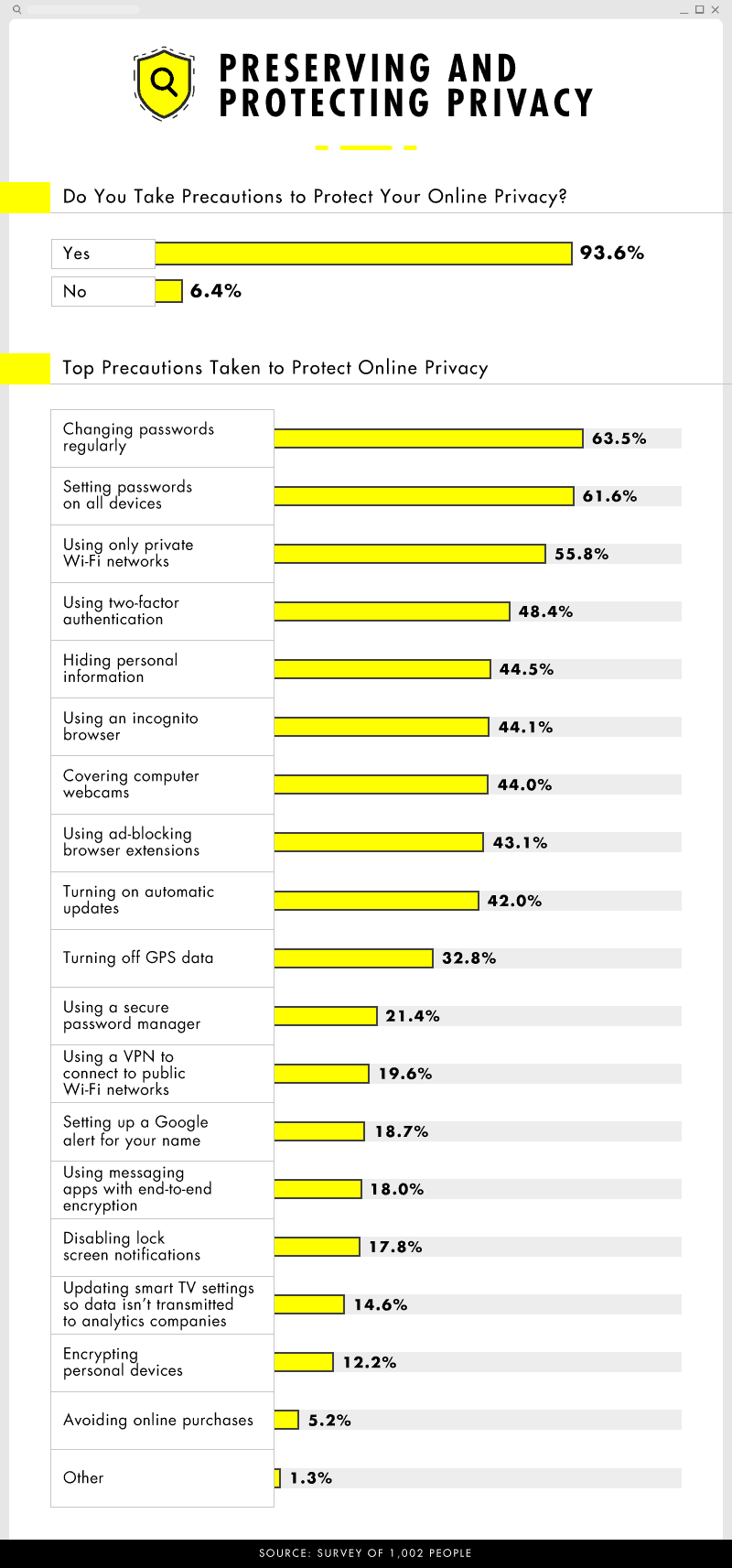 Nearly all respondents (94%) took some effort to protect themselves online, with only 6% admitting to taking no precautions to protect their online privacy.
Nearly all respondents (94%) took some effort to protect themselves online, with only 6% admitting to taking no precautions to protect their online privacy. Nearly half of people said they were most protective of identification, such as a driver’s license and passport.
Nearly half of people said they were most protective of identification, such as a driver’s license and passport. 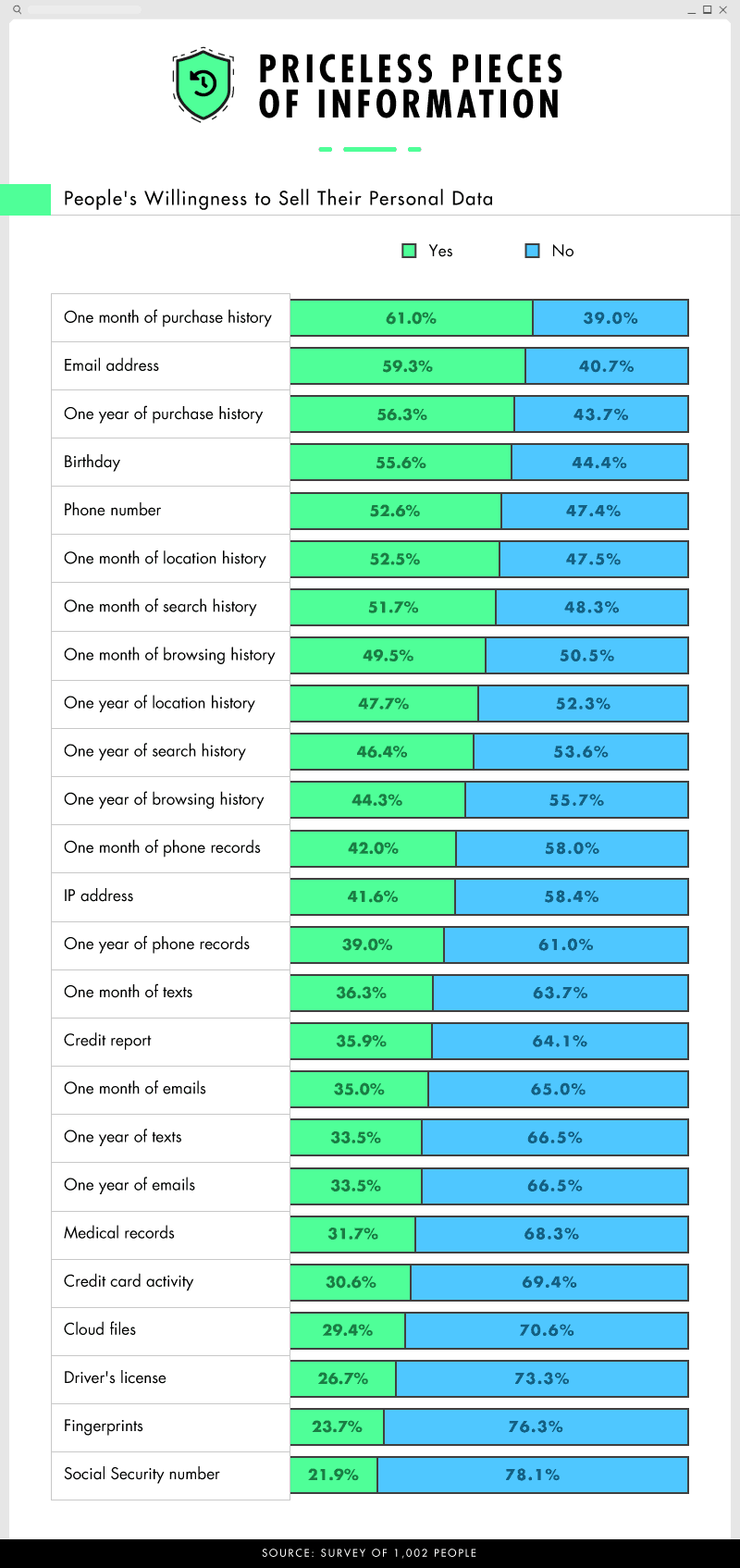
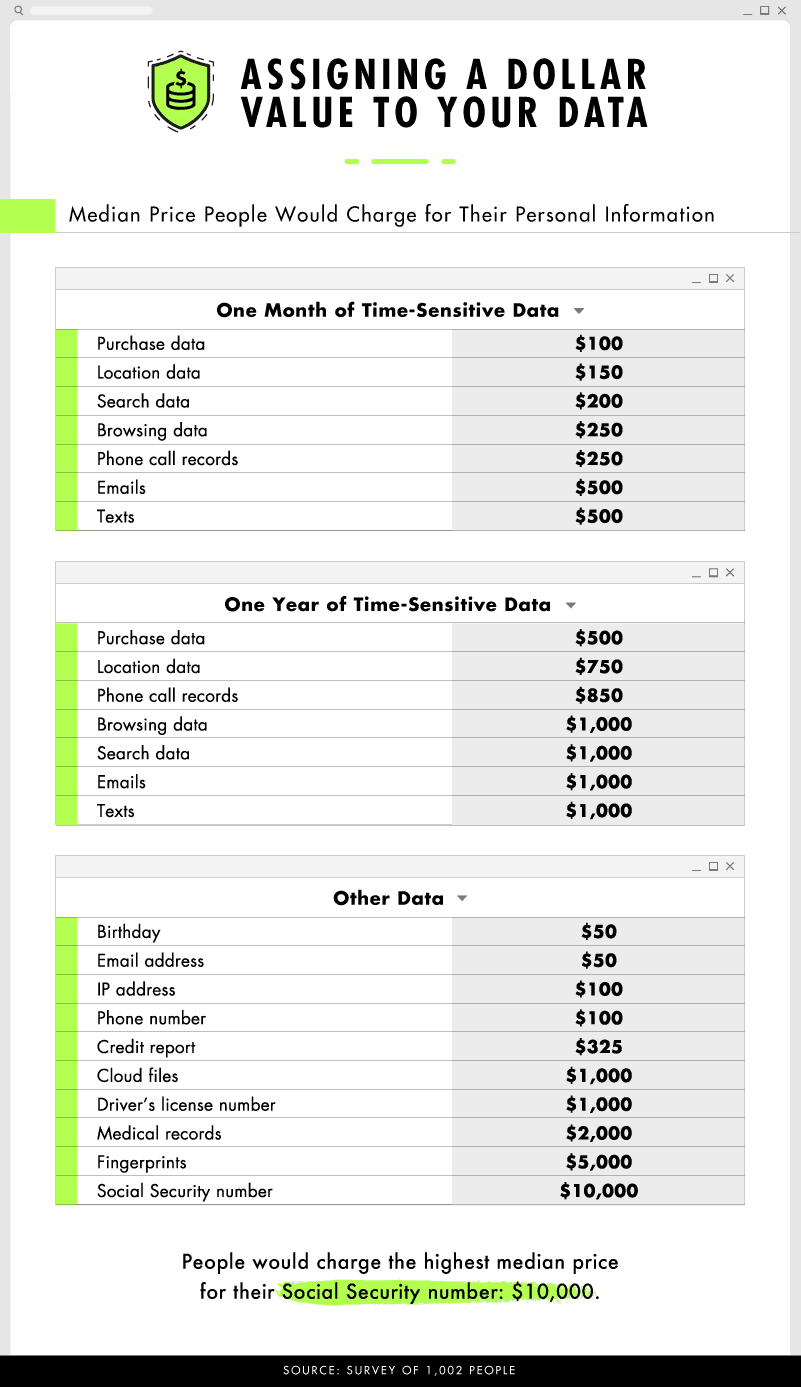 We found that people tended to greatly overestimate the value of their data.
We found that people tended to greatly overestimate the value of their data.
 And since most of these entities are attractive targets for attackers, it makes the bugs all that more critical.
And since most of these entities are attractive targets for attackers, it makes the bugs all that more critical.